It’s used in the air transport industry, now its used in pandemic defense models. The swiss cheese model or risk management just as useful in internet security. Talking to a client about why one might use the various systems of defense I realized this is a great place to start with a long series of IT security tips. So, I think I’m going to use it to kick off my security tip series of blogs. These are written to share with customers so I may not need to always rewrite. I like to write so I often compose emails based on following up in person discussion.
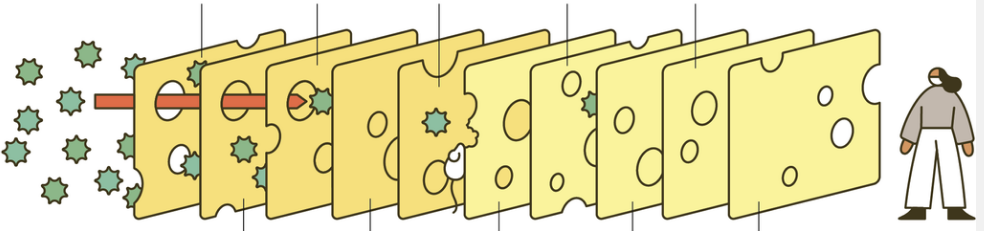
In this swiss cheese layered defense against virus/pathogen particles I edited out the labels for each layer of cheese … ahem, internet security. There are many names for the attacks … but they are often confusing. Forgive me but I’ve lead from one type of attack to another.
Vectors – how they get through the holes – lets assume its not always a straight line or they might get part way in and then find another vector to get the rest of the way into “installed malicious or unauthorized software”. Trojans are more about how you get the software through the swiss cheese so they are a “vector” of sorts.
Malware – one name for pathogens aka “malicious or unauthorized software” – mal for malicious so lets assume the worst. Sometimes healthy tools used maliciously are referred to as …
PUP – potentially unwanted programs. They can be malicious or dangerous – or they might be ..
Hijacks – rewriting things that redirect your internet search or URL requests to somewhere else that steals or fakes itself as a …

Man in the Middle – something that doesn’t always pass on the real information in a communication. It can capture your credentials and log in, a bit like an attack where they put a fake front on an ATM that actually operates the real ATM at the back, real money comes out but it is capturing your card and pin and later they use this to rob your account.
Free or Pirated software – is a way that virus, malware, PUP, man in the middle all can come together. When I was a kid I freely downloaded a ton of free software all the way back before the internet. Even then viruses like the “magic mushroom” virus – it was a cool program that made digitized sound from the humble PC speaker. People thought, “what, really? Is that even possible?” – and tested it, it worked and shared it with friends and on “bulletin boards” and so that virus got spread as widely as interest in this tech.
So don’t pirate software because your antivirus is highly unlikely to catch ALL the malware. They might put an obvious one and a custom one you can’t find that pwns (think owns but more severe) your operating system.
Security Tip #1 – The swiss cheese model needs several layers – we can help you
Hire people who understand this swiss cheese model of security to give you layers that you probably don’t know about. I can write tips and share the knowledge freely but for example you may want to buy a firewall. Its no good if you can’t buy it from the right people and trust them to do it right. That is what we want to establish ourselves as for you – a trusted provider who reveals the risks and helps you put in plaselayers to block them .
So … watch this space for more Tips and this means subscribe … and this swiss cheese model will be built out one layer at a time. You can do it yourself to some degree, and you must but other layers you must necessarily farm out to a provider or its going to be disabled if your computer gets infiltrated as swiftly as they find your passwords. Having a provider that logs in separately and with 2FA or from a secured location only will give you some final layers of defense and potential notifications that something is going wrong.

One thought to “Security Tip #1: The Swiss Cheese Model”
Well explained